Why Fiber Network Security Is Critical for Protecting Sensitive Data and Communications
Why Fiber Network Security Is Critical for Protecting Sensitive Data and Communications
Blog Article
The Important Function of Information and Network Safety And Security in Shielding Your Information
In a period where information breaches and cyber risks are significantly common, the relevance of durable data and network security can not be overemphasized. Organizations must not only protect delicate details yet also make sure conformity with advancing governing requirements. The implementation of reliable security measures, such as file encryption and gain access to controls, is vital to keeping count on and functional honesty. The landscape of cyber threats is continuously moving, elevating questions about the adequacy of existing methods and what brand-new techniques might be required to remain ahead of prospective threats. What lies ahead in this complex protection setting?
Comprehending Data Security
In today's digital landscape, a frustrating bulk of companies face the complexities of data security. This vital element of infotech involves shielding sensitive information from unapproved accessibility, corruption, or theft throughout its lifecycle. Information protection includes various strategies and innovations, including security, gain access to controls, and data masking, all aimed at safeguarding information versus violations and vulnerabilities.
An essential aspect of information safety and security is the identification and category of information based on its level of sensitivity and importance. This category helps organizations prioritize their protection initiatives, assigning sources to secure the most critical information properly. In addition, carrying out robust plans and treatments is necessary to ensure that employees understand their role in keeping information security.
Regular audits and evaluations aid in identifying possible weak points within a company's data safety framework. Furthermore, staff member training is essential, as human mistake continues to be a substantial variable in information violations. By cultivating a society of safety understanding, organizations can mitigate risks connected with insider dangers and carelessness.
Significance of Network Safety And Security
Network security stands as a foundation of an organization's general cybersecurity strategy, with about 90% of companies experiencing some kind of cyber hazard in recent times. The relevance of network safety hinges on its capacity to shield delicate details and preserve the honesty of organization procedures. By protecting network infrastructures, companies can avoid unauthorized access, data violations, and various other malicious tasks that could jeopardize their possessions and credibility.
Executing robust network safety measures not just assists in mitigating dangers but additionally promotes trust among stakeholders and clients. When clients are guaranteed that their monetary and individual info is secure, they are most likely to engage with the company, leading to boosted customer loyalty and business development.
Additionally, a well-structured network safety and security framework facilitates compliance with various governing demands. Organizations must comply with market standards and legal mandates worrying data defense, and effective network safety and security techniques can make certain compliance, thus staying clear of potential penalties.
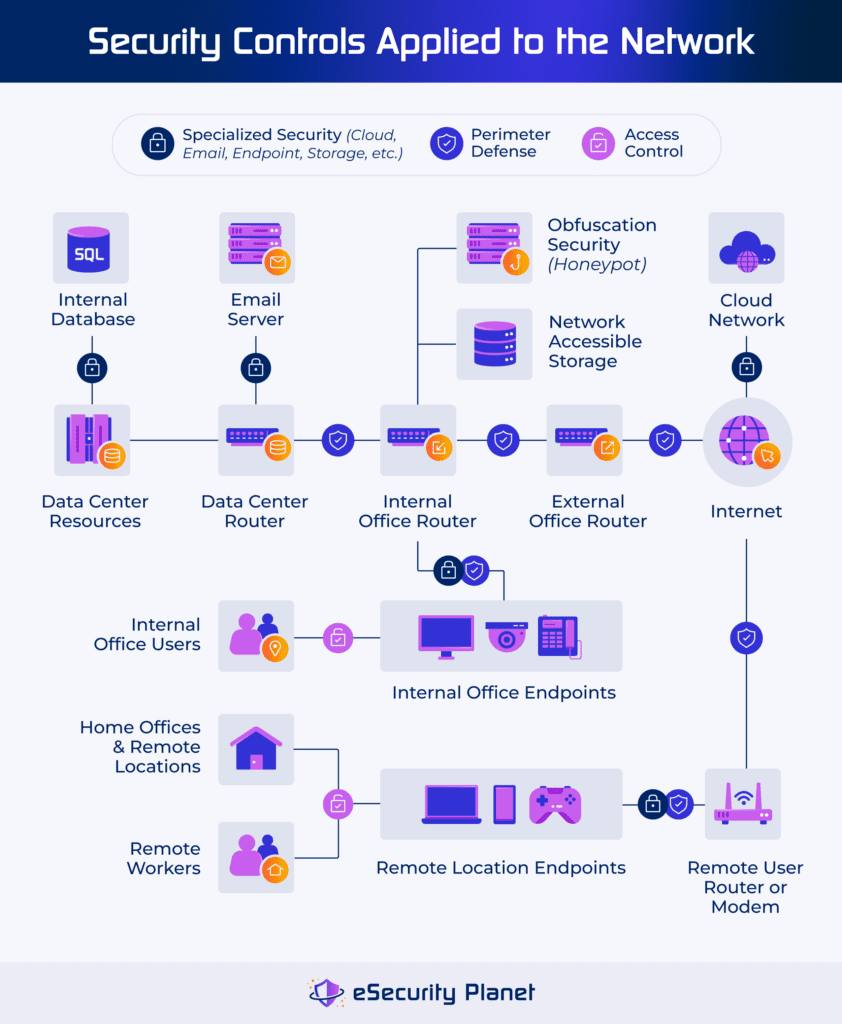
Typical Cyber Risks
Organizations have to stay watchful versus a variety of cyber risks that can weaken their network security initiatives. Among the most typical hazards is malware, which encompasses viruses, worms, and ransomware that can interfere with operations, swipe data, or hold info captive. Phishing attacks, where malicious stars pose relied on entities to deceive people into exposing sensitive info, continue to expand in sophistication, making user education and learning crucial.
Another common risk is dispersed denial-of-service (DDoS) strikes, which overload systems with traffic, making them inaccessible to genuine individuals. Insider risks, whether read more deliberate or unintended, pose significant threats as staff members may inadvertently expose sensitive data or intentionally exploit their accessibility for destructive functions.
Additionally, vulnerabilities in software program and hardware can be made use of by cybercriminals, highlighting the value of normal updates and spot monitoring. Social design strategies further complicate the landscape, as assaulters adjust individuals into disclosing secret information with emotional control.
As these risks advance, organizations have to preserve an aggressive Discover More method to determine, reduce, and respond efficiently to the ever-changing cyber threat landscape, protecting their useful details and maintaining count on with stakeholders. fft pipeline protection.
Ideal Practices for Security
Implementing robust safety measures is essential for protecting sensitive details and keeping operational stability. Organizations should begin by carrying out comprehensive threat analyses to identify susceptabilities within their systems. This positive technique allows the prioritization of security campaigns tailored to the specific demands of the organization.
Taking on strong password plans is important; passwords must be complicated, routinely altered, and handled utilizing secure password management tools. Multi-factor verification (MFA) includes an additional layer of safety by calling for additional verification methods, therefore lowering the threat of unauthorized accessibility.
Regular software updates and patch management are important to shield against understood susceptabilities. Executing firewall softwares and invasion detection systems can additionally secure networks from external risks. Worker training is similarly essential; staff must be enlightened on identifying phishing efforts and comprehending the relevance of information safety protocols.
Information encryption must be employed for sensitive details, both at remainder and en route, to make sure that also if information is intercepted, it continues to be unattainable (fft pipeline protection). Last but not least, organizations have to create and on a regular basis test event reaction prepares to guarantee swift action in the event of a security breach. By adhering to these best practices, organizations can enhance their protection stance and shield their vital information possessions
Future Trends in Safety And Security
The landscape of data and network security is continuously advancing, driven by developments in technology and the enhancing sophistication of cyber hazards. As organizations progressively adopt cloud computing and IoT tools, the paradigm of safety will certainly move towards a zero-trust design. This method emphasizes that continue reading this no entity-- outside or interior-- is naturally trusted, mandating confirmation at every gain access to factor.
Additionally, the usage of fabricated intelligence and artificial intelligence in protection protocols is on the surge. These modern technologies enable predictive analytics, enabling organizations to recognize vulnerabilities and prospective threats before they can be exploited. Automation will likely play a pivotal role in streamlining safety and security responses, decreasing the time taken to mitigate violations.
Additionally, regulatory structures will remain to tighten, requiring a lot more strict conformity actions. Organizations has to stay abreast of evolving policies to ensure they satisfy safety and security requirements.

Conclusion
To conclude, the relevance of information and network security can not be overemphasized in the modern electronic landscape. With the prevalence of cyber risks and the raising intricacy of regulatory demands, companies need to embrace thorough security steps to secure delicate information. By staying and executing efficient strategies notified regarding emerging fads, services can boost their resilience versus prospective assaults, guaranteeing information integrity and cultivating trust among stakeholders and clients. Prioritizing security continues to be necessary for operational continuity and lasting success.
In a period where information violations and cyber risks are progressively prevalent, the importance of durable information and network safety and security can not be overstated. Information protection includes various strategies and technologies, consisting of security, gain access to controls, and data masking, all aimed at securing details versus violations and vulnerabilities.
A basic element of data safety and security is the identification and classification of data based on its sensitivity and value.The landscape of information and network protection is continually advancing, driven by improvements in modern technology and the raising refinement of cyber dangers.In conclusion, the relevance of information and network protection can not be overstated in the contemporary electronic landscape.
Report this page